Return oriented programming (ROP) Protector
A radical defense solution that protects legacy software systems from ROP cyberattacks
ROP Protector is a radical defense solution that protects legacy systems from ROP cyberattacks. The cybersecurity playing field is fundamentally asymmetric. Attackers can easily identify weaknesses in a target system as soon as they have access to its code and configuration. As a result, defenders are perpetually playing a game of catch-up after an attack has occurred to secure their systems.
The ROP attack technique effectively uses code already present within the target system to carry out the attack. ROP attackers harness software components within the legacy system, commonly referred to as gadgets, to carry out the attack. Once devised, ROP attacks are easy to carry out since they rely on the target system being static. ROP Protector is an efficient and practical solution to the ROP defense needs of legacy systems.
The ROP attack technique effectively uses code already present within the target system to carry out the attack. ROP attackers harness software components within the legacy system, commonly referred to as gadgets, to carry out the attack. Once devised, ROP attacks are easy to carry out since they rely on the target system being static. ROP Protector is an efficient and practical solution to the ROP defense needs of legacy systems.
|
Anchor Element Copy for linking on the same page:
https://www.peratonlabs.com/?data-scroll-to-anchor=HowItWorks
Copy for linking from an external page:
https://www.peratonlabs.com/?data-anchor-link=HowItWorks
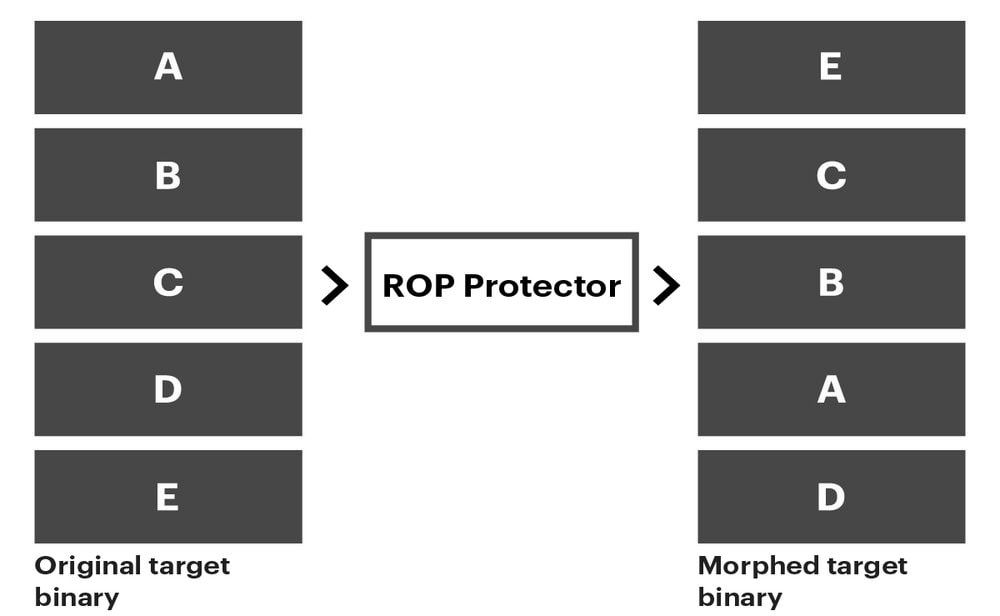
How it worksROP cyberattacks are easy to accomplish because target systems are essentially static. ROP Protector is a moving target defense solution which ensures that the target system itself is dynamic—preventing attacks that aim to leverage static gadgets within the system. ROP Protector creates a morphed version of the target system that has exactly the same set of capabilities as the original yet does not have the gadgets that the ROP attack depends on.
ROP Protector is a pure binary-to-binary code scrambling solution. It does not require access to the source code for the protected system. It ensures that gadgets needed to facilitate a typical ROP attack are not available for use by an attacker. Importantly, studies have shown that well-known applications (e.g., the Apache webserver) transformed by ROP Protector have comparable performance to their original versions. ROP Protector is particularly valuable in the case of legacy systems for which source code is unavailable since it is a pure binary-to-binary code scrambling solution. Studies have shown that neither the capabilities nor the performance of well-known applications (e.g. the Apache webserver) are impacted after being scrambled by ROP Protector. Thus, ROP Protector is an efficient and practical capability for the ROP defense needs of legacy systems. Anchor Element Copy for linking on the same page:
https://www.peratonlabs.com?data-scroll-to-anchor=features
Copy for linking from an external page:
https://www.peratonlabs.com?data-anchor-link=features
Features
Anchor Element Copy for linking on the same page:
https://www.peratonlabs.com/?data-scroll-to-anchor=Advantages
Copy for linking from an external page:
https://www.peratonlabs.com/?data-anchor-link=Advantages
Advantages
Anchor Element Copy for linking on the same page:
https://www.peratonlabs.com?data-scroll-to-anchor=resources
Copy for linking from an external page:
https://www.peratonlabs.com?data-anchor-link=resources
ResourcesAnchor Element Copy for linking on the same page:
https://www.peratonlabs.com/?data-scroll-to-anchor=links
Copy for linking from an external page:
https://www.peratonlabs.com/?data-anchor-link=links
Research and products of interestResearch
Products
Anchor Element Copy for linking on the same page:
https://www.peratonlabs.com?data-scroll-to-anchor=requestinfo
Copy for linking from an external page:
https://www.peratonlabs.com?data-anchor-link=requestinfo
|